Instructor’s guide — How to see submissions and access Similarity & AI reports
PlagiarismCheck
APRIL 25, 2024
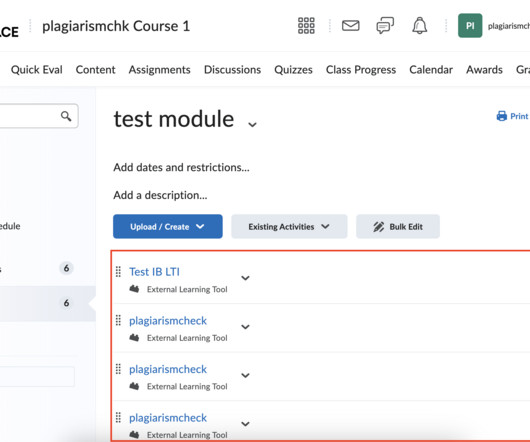
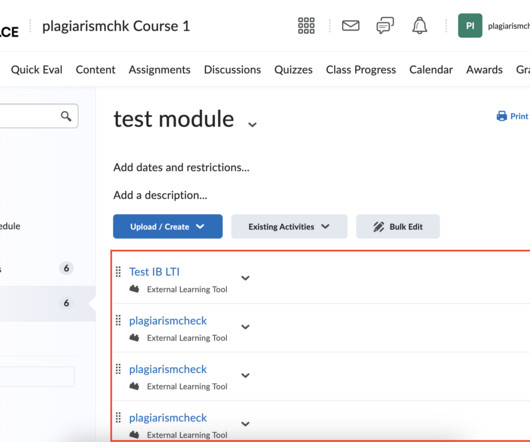
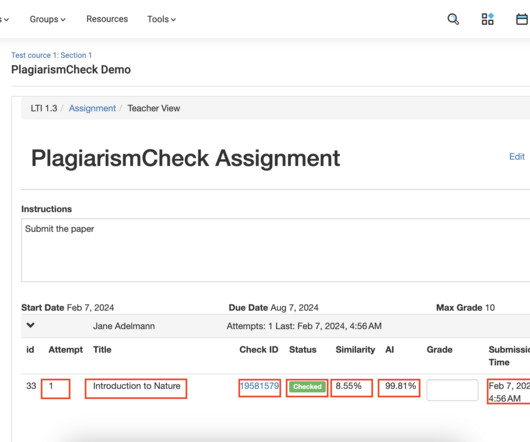
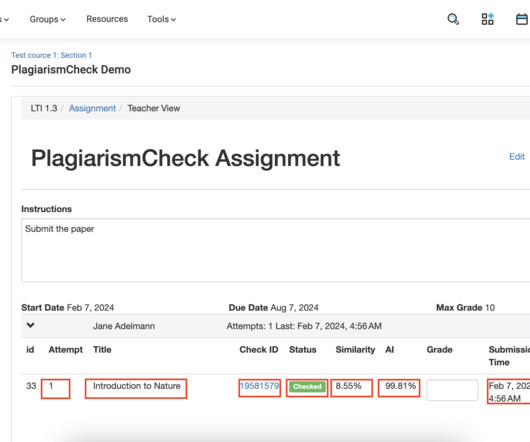
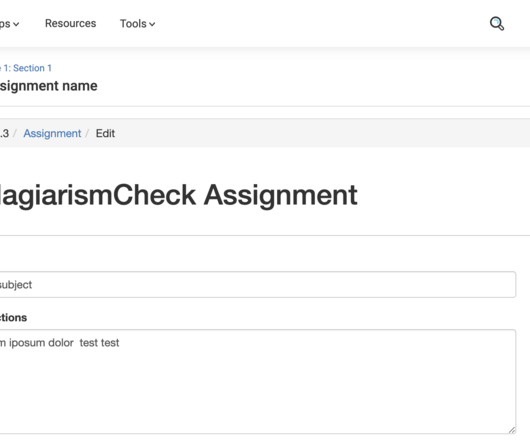
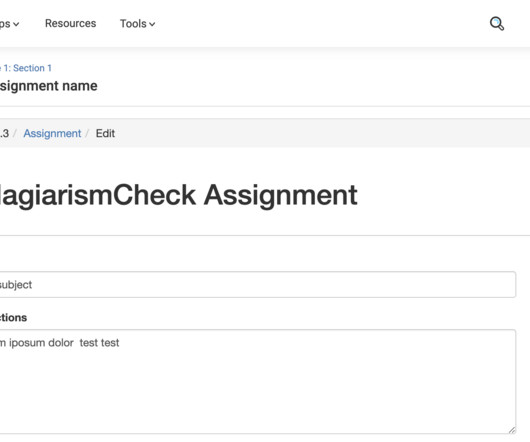
This guide explains how to view students’ submissions in your assignments. Open an assignment created through External Tool where students were supposed to submit their works (to access them follow Course —> Select a Module —> Select an assignment). Check ID — a unique identifier of a Similarity & AI report in our system.




































Let's personalize your content