Cyberattacks on Ed-Tech Companies Rare, But Hugely Disruptive, Report Finds
Cyberattacks carried out directly against ed-tech vendors, while rare, tend to have an especially severe impact on K-12 because they affect a large swath of students across multiple school districts at the same time, a federal report has found.
The Government Accountability Office, an independent watchdog agency that conducts investigations for Congress, was asked to look into the vulnerability of student, teacher and administrator data as more schools than ever before utilize online tools because of the mass shift to distance learning due to COVID-19.
In a recently released report, the agency analyzed 99 school data breaches over the past four years that compromised the personal information of K-12 students in about 287 districts.
In doing so, the GAO also acknowledged the 99 data breaches it counted more than likely underrepresents the total number of successful hacks that occurred during that period.
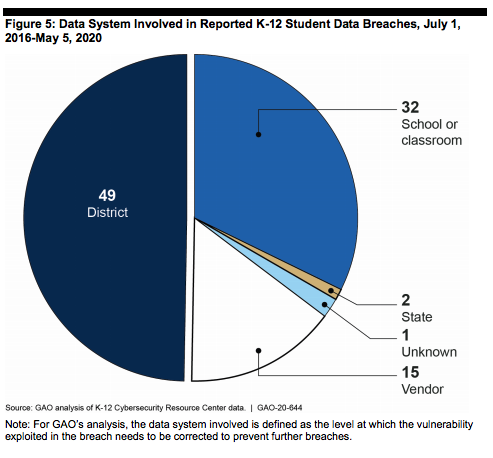
One of the agency’s conclusions: breaches of district, school or classroom data systems were the most common, followed by vendor system hacks. Nearly half of the student data breaches involved district data systems, a third involved school or classroom data systems, and vendor systems were linked to 15 breaches.
From the report:
“Vendors typically have many school districts using their products. As a result, a vulnerability in the technology that leads to a data breach can affect thousands of students. In one breach by an unknown actor, a learning assessment platform exposed the personally identifiable information (PII) of students with accounts, including their names and birthdates.”
Of those 15 cyberattacks connected to ed-tech vendors, five involved more than one district.
In one instance, the report cites a breach from last school year against an ed-tech vendor system that affected 135 school districts.
And while students and staff are most responsible for K-12 data breaches, the GAO notes that ed-tech vendor error can also play a role. According to the report, the federal watchdog agency counted two occasions where vendors were liable for data breaches.
Both incidents were accidental, according to the report, which did not provide any further detail on those examples.
‘Zoombombings’ on the Rise
The report also issued a warning about a new Covid-era type of cyberattack: “Zoombombings” — a term that refers to when videoconferences, on any platform, are breached by intruders.
More than two-dozen instances of breaches involving K-12 classroom video conferences were tallied between April and May of this year, according to the GAO. In one incident, 50 elementary school students were exposed to pornography during a virtual class, and in another high school students were targeted with hate speech during a class, resulting in the cancellation that day of all classes using the videoconferencing software.
“These incidents also raise concerns about the potential for violating students’ privacy,” the report said. “For example, one district is reported to have instructed teachers to record their class sessions Teachers said that students’ full names were visible to anyone viewing the recording.”
K-12 Hacks ‘Difficult to Fully Know or Track’
The GAO relied on a private database of cyber attacks and leaks collected by Doug Levin of EdTech Strategies for it’s report. School districts are not required to report data breaches, so the federal agency analyzed data from July 2016 through early May 2020 cataloged by Levin’s K-12 Cybersecurity Resource Center, which the GAO describes as the “most complete resource that tracks K-12 cybersecurity incidents.”
But the agency used a different methodology for counting cyberattacks, resulting in a big discrepancy between what the GAO’s total number of breaches during that four-year period versus the center’s count. Levin’s organization tallied more than 450 breaches during that time, compared to the GAO’s 99.
That’s due to the GAO counting each attack as one incident even if multiple school districts were involved. On the other hand, Levin’s organization counted each district data breach separately, regardless if they were all victims of the hack.
The GAO notes that “in the case where the breach of a large vendor’s data system affected at least 135 school districts, CRC counted this breach as 135 separate incidents, while we considered the incident to be one breach. For these reasons, our incident counts are lower than CRC’s public counts.”
In the report, the federal agency touched on the difficulty of trying to accurately assess the number of K-12 cyberattacks, citing one case where personal information for hundreds of thousands of current and former students in a district was publicly exposed for two years before the breach was noticed.
“The 99 reported student data breaches likely understate the number of breaches that occurred, for different reasons,” the GAO wrote. “Reported incidents sometimes do not include sufficient information to discern whether data were breached … In addition, breaches can go undetected for some time.”
Follow EdWeek Market Brief on Twitter @EdMarketBrief or connect with us on LinkedIn.
See also: